What is a Firewall? Your First Line of Defense in Cyber security !
In an increasingly interconnected digital world, What is a Firewall? Your First Line of Defense in Cybersecurity! cyber security has become a paramount concern for individuals, businesses, and governments alike. Among the array of tools and strategies designed to safeguard sensitive information and maintain secure communication, the firewall stands out as a fundamental component. As the first line of defense in cybersecurity, firewalls play a crucial role in protecting networks from unauthorized access, malicious software, and cyberattacks. This article delves deep into the concept of firewalls, their types, functionality, and significance in a comprehensive cybersecurity strategy.

Understanding Firewalls
A firewall is a network security device—either hardware, software, or a combination of both—that monitors and controls incoming and outgoing network traffic. By enforcing predefined security rules, firewalls act as a barrier between trusted internal networks and untrusted external networks, such as the internet. The primary purpose of a firewall is to permit legitimate traffic while blocking potentially harmful or unauthorized data transmissions.
What is a Firewall? Your First Line of Defense in Cybersecurity!
The concept of firewalls dates back to the late 1980s, coinciding with the rise of the internet. Early firewalls were simple packet filters that analyzed data packets based on predefined rules, such as IP addresses and ports. What is a Firewall? Your First Line of Defense in Cybersecurity! Over time, firewalls have evolved into sophisticated tools that offer advanced features like deep packet inspection, application-layer filtering, and intrusion prevention systems (IPS).
How Does a Firewall Work?
At its core, a firewall functions by inspecting data packets that travel to and from a network. These packets contain information such as the source and destination addresses, protocols, and content.What is a Firewall? Your First Line of Defense in Cybersecurity! Based on predefined rules or dynamic policies, the firewall decides whether to allow, deny, or log the traffic.
The primary modes of operation for firewalls include:
- Packet Filtering: This is the simplest form of firewall operation. The firewall examines the headers of data packets What is a Firewall? Your First Line of Defense in Cybersecurity! and determines whether they meet specific criteria (e.g., source IP address, destination IP address, port number). Packets that do not meet the criteria are dropped.
- Stateful Inspection: Also known as dynamic packet filtering, this method tracks the state of active connections and uses this information to decide which packets to allow or block. What is a Firewall? Your First Line of Defense in Cybersecurity! It ensures that only packets belonging to established sessions are permitted.
- Proxy Service: Proxy firewalls act as intermediaries between users and the internet. They inspect incoming and outgoing data at the application layer, making them highly effective at detecting and blocking malicious content.
- Next-Generation Firewalls (NGFW): These advanced firewalls combine traditional packet filtering with additional capabilities such as deep packet inspection, intrusion detection systems (IDS), and intrusion prevention systems (IPS). NGFWs are particularly effective against modern, complex threats.
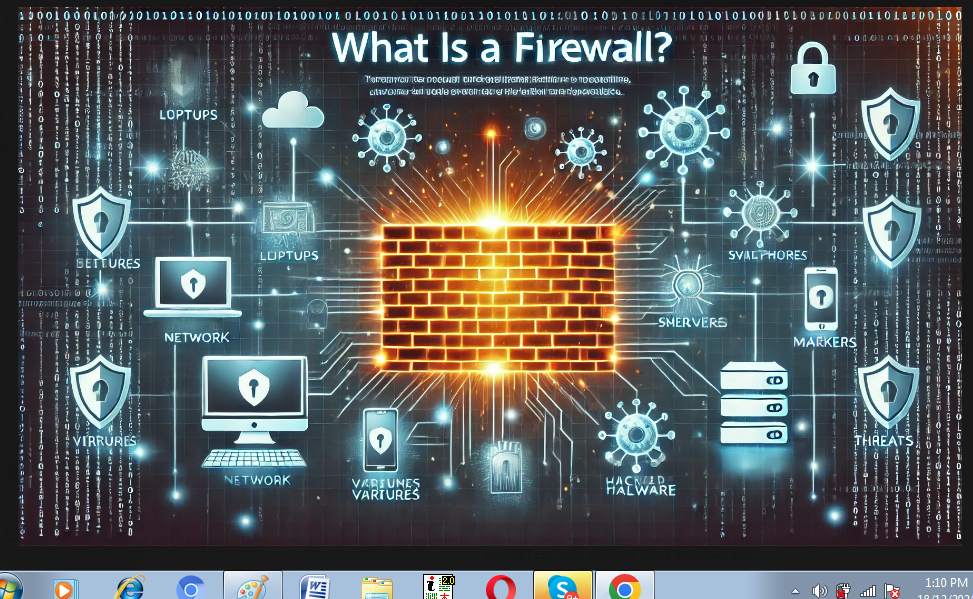
Types of Firewalls
Firewalls come in various forms, What is a Firewall? Your First Line of Defense in Cybersecurity! each tailored to meet specific security requirements. The most common types include:
- Hardware Firewalls:
- These are physical devices installed between a network and the internet.
- Often used by organizations to protect entire networks, hardware firewalls offer robust performance What is a Firewall? Your First Line of Defense in Cybersecurity! and centralized control.
- Examples include Cisco ASA, Fortinet FortiGate, and Palo Alto Networks appliances.
- Software Firewalls:
- Installed on individual devices, software firewalls provide granular control over application-level traffic.
- Commonly used by individuals and small businesses, What is a Firewall? Your First Line of Defense in Cybersecurity! they are ideal for protecting endpoints such as laptops, desktops, and mobile devices.
- Examples include Windows Defender Firewall and ZoneAlarm.
- Cloud-Based Firewalls (Firewall as a Service – FWaaS):
- Hosted in the cloud, these firewalls are scalable and offer seamless integration with modern cloud environments.What is a Firewall? Your First Line of Defense in Cybersecurity!
- Particularly useful for businesses with distributed networks or remote workforces, cloud-based firewalls provide flexible and cost-effective security.
- Next-Generation Firewalls (NGFW):
- NGFWs integrate traditional firewall features with advanced capabilities like application awareness, malware detection, and advanced threat protection.
- They are highly effective against sophisticated cyber threats and are widely adopted in enterprise environments.
- Network Address Translation (NAT) Firewalls:
- These firewalls hide private IP addresses within a network by translating them into a single public IP address.
- By concealing internal network details, NAT firewalls enhance security and reduce the risk of direct attacks.
Key Features of Modern Firewalls
Modern firewalls offer a range of features designed to provide comprehensive protection against an array of cyber threats. Some of the key features include:
- Deep Packet Inspection (DPI):
- Analyzes the content of data packets beyond the header, enabling detection of malicious payloads and suspicious activities.
- Intrusion Detection and Prevention:
- Monitors network traffic for signs of malicious activity and takes proactive measures to block or mitigate threats.
- Application Awareness:
- Identifies and controls applications running on a network, allowing administrators to enforce policies specific to each application.
- Virtual Private Network (VPN) Support:
- Facilitates secure remote access by encrypting data transmitted between users and the network.
- Content Filtering:
- Blocks access to inappropriate or harmful websites based on categories or specific URLs.
- Logging and Reporting:
- Provides detailed logs and reports of network activity, enabling administrators to identify trends, analyze incidents, and optimize security policies.
Importance of Firewalls in Cybersecurity
Firewalls are indispensable in the modern cybersecurity landscape. Their significance stems from their ability to:
- Prevent Unauthorized Access:
- By blocking unauthorized attempts to access a network, firewalls protect sensitive information and critical systems.
- Mitigate Malware and Virus Spread:
- Firewalls prevent the spread of malicious software by filtering out harmful data packets.
- Safeguard Against Cyberattacks:
- Firewalls defend against various cyber threats, including Distributed Denial of Service (DDoS) attacks, phishing, and ransomware.
- Enhance Regulatory Compliance:
- Many industries require organizations to implement firewalls as part of their compliance with data protection regulations, such as GDPR, HIPAA, and PCI DSS.
- Provide Peace of Mind:
- For individuals and businesses, knowing that a robust firewall is in place fosters confidence in the security of their digital assets.
Common Challenges and Limitations
While firewalls are vital, they are not without challenges. Common issues include:
- Configuration Complexity:
- Improperly configured firewalls can create vulnerabilities or disrupt legitimate traffic.
- Performance Impact:
- Advanced features like deep packet inspection can introduce latency, affecting network performance.
- Limited Scope:
- Firewalls cannot protect against threats that bypass them, such as phishing emails or insider threats.
- Regular Maintenance:
- Firewalls require frequent updates and monitoring to remain effective against evolving threats.
Best Practices for Using Firewalls
To maximize the effectiveness of firewalls, adhere to these best practices:
- Regularly Update Rules and Policies:
- Ensure firewall rules are up-to-date and reflect the latest security requirements.
- Implement Layered Security:
- Combine firewalls with other security measures, such as antivirus software, intrusion detection systems, and endpoint protection.
- Monitor and Audit Logs:
- Regularly review firewall logs to identify unusual activities and respond promptly to incidents.
- Enable Alerts:
- Configure alerts for critical events, such as repeated failed access attempts or detected malware.
- Train Users:
- Educate employees and users about cybersecurity best practices to reduce the likelihood of human error.
The Future of Firewalls
As cyber threats continue to evolve, so too must firewalls. Emerging trends and technologies shaping the future of firewalls include:
- Artificial Intelligence and Machine Learning:
- AI-powered firewalls can analyze vast amounts of data in real time, identifying patterns and anomalies to detect threats more effectively.
- Zero Trust Architecture:
- Firewalls will play a critical role in implementing zero trust principles, ensuring strict verification for every user and device attempting to access network resources.
- Integration with Cloud Security:
- As businesses adopt cloud computing, firewalls are being integrated with cloud-native security solutions to provide seamless protection for hybrid environments.
- IoT Security:
- Firewalls are being enhanced to address the unique challenges posed by the proliferation of Internet of Things (IoT) devices.
Conclusion
A firewall is much more than a barrier; it is a dynamic, adaptive shield that safeguards networks against an ever-growing array of cyber threats. As the cornerstone of any comprehensive cybersecurity strategy, firewalls provide indispensable protection for individuals and organizations alike. By understanding how firewalls work, their types, and their significance, users can make informed decisions about implementing this critical technology. In an age where digital security is paramount, a well-configured firewall truly stands as your first line of defense.